Written by Matthew Sharp, CISO at Logicworks
Russia has a long history of leveraging cyber attacks to advance national interests. Various sources have attributed cyber activities to Russia claiming their intended purpose was to redirect attention, influence political processes, inject mis-information, damage critical infrastructure, and take systems off-line. 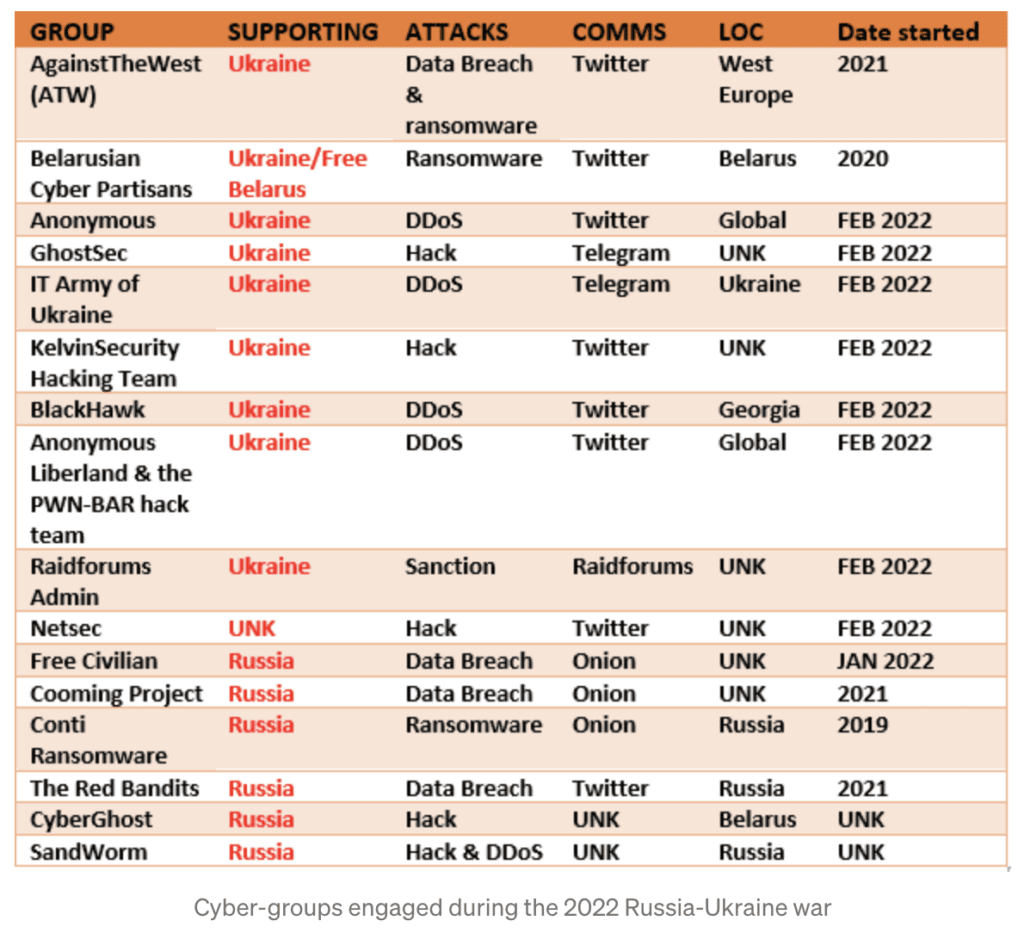
Meanwhile, ransomware and recent judgements have caused Lloyd’s of London and other insurers to take steps to exclude from coverage and create more explicit terms for what counts as an “act of war.” Further, in the past year we have seen premiums for cybersecurity liability coverage skyrocket by 300-800%, and in some cases companies have been denied coverage altogether resulting in a need to ‘self-insure’ what was once considered a low probability / high impact risk profile typically treated with risk transference strategies.
Top 5 Actions You Can Take
In response to the current geopolitical conflict and evolving insurance markets, Logicworks has prepared a list of the Top 5 Actions you can take to ensure a more resilient cloud workload:
1. Multi-factor Authentication
CISA recommends several actions to “Reduce the likelihood of a damaging cyber intrusion” including application of MFA. We agree! Historically best practices might have limited the use of MFA to remote access or privilege accounts, but now is the time to expand the use of MFA to include all access including your email, VPN, system/site administration, etc.
2. Distributed Denial of Service (DDoS) Protection
The evidence is clear that Russia will employ DDoS attacks to impact the critical infrastructure including healthcare and financial services of its perceived adversaries. Logicworks recommends ensuring that internet-facing infrastructure is resilient to DDoS attacks. One way to easily enhance resilience is to enable AWS Shield and AWS WAF on workloads hosted in the public cloud.
3. Malware Protection
By studying the NotPetya attack of 2017, you will understand that Russia has previously utilized destructive malware. That malware has had far reaching effects including collateral damage resulting in a $1.4B settlement with Merck that was only recently settled. Thus it is important to have a combination of both observability (ThreatStack) and malware prevention controls in place (TrendMicro).
4. Egress Filtering
Common advanced persistent threats will employ Remote Code Execution (RCE) attacks. That is precisely why a multi-dimensional defense strategy is critical. In this case, even if you miss the attack on the way in, you may be clued into the presence of an attacker as they look to establish a foothold by making contact with the outside world. Recent Apache Log4j vulnerabilities make this style attack very likely. However, beware that merely noticing data leaving your network is too little, too late. What’s really required is to both create awareness of anomalous outbound traffic, AND block it before an attacker is able to exfiltrate sensitive information.
5. Enhanced Logging – Enable VPC Flow Logs, Cloud Trail, & XDR
Retaining a clear record of network traffic, actions at the cloud management plane, and events happening inside the compute nodes in your network are critical. As a result, we recommend full stack observability is important. Wherever possible create and retain a complete view of actions taken at the cloud network, management layer, compute, container, and application layer.In most cases this requires a variety of tools, and our advice is to use highly integrated platform solutions wherever possible. If done correctly, whenever Indicators of Compromise (IOCs) are released you will be able to conclusively indicate to your executive leadership team, “no we were not affected by that attack.”
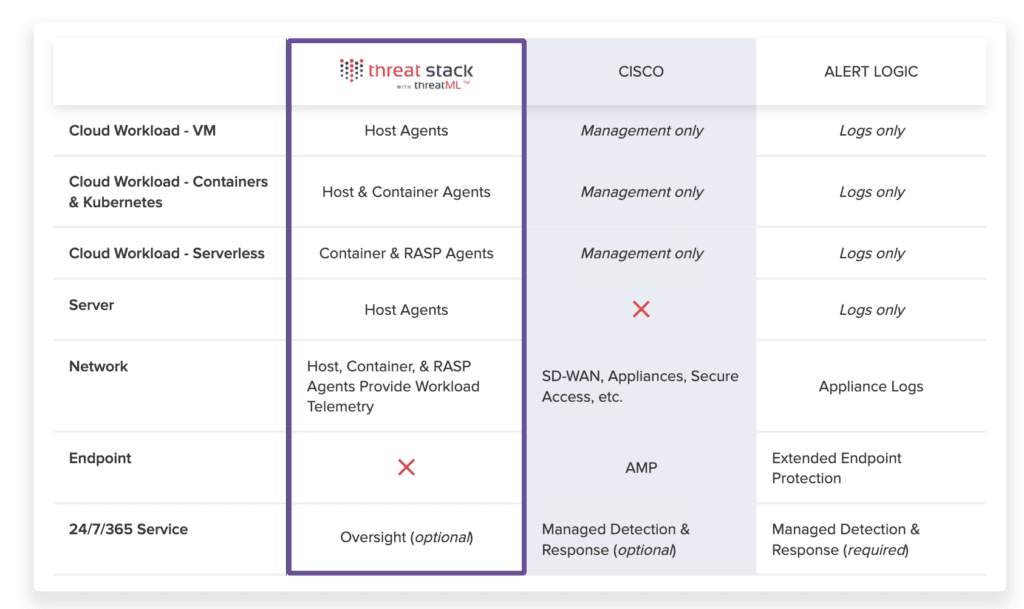
If you’re interested in learning more about cloud security, we highly encourage you to reach out to Logicworks for a Well-Architected Review or Security Assessment. We can help you identify gaps in your current architecture and priorities for remediation. We look forward to hearing from you.


No Comments