If you’re running on the public cloud and already use network access control lists (ACLs) and security groups, do you need to invest in a Web Application Firewall (WAF)?
In this post, we’ll break down each of these technologies one by one and recommend the best tools for your use case.
What’s a WAF?
A Web Application Firewall (WAF) monitors HTTP(S) Layer 7 traffic and protects your applications and APIs from common web exploits. Amazon or Microsoft Azure’s WAF service will work with applications that receive traffic via a Content Delivery Network (CDN), API gateway, or Application Load Balancer. In IaaS, a WAF can be enabled with a few clicks in your platform’s console.
How’s a WAF different from network ACLs or security groups?
In most IaaS platforms, when you create a network, it automatically generates an Access Control List (ACL). An ACL is essentially a list of ALLOW or DENY rules that control access to your network. It’s very basic; no dynamic protections or alerting, just traffic control for HTTP(S), TCP, RDP, MySQL, etc. Whenever you create a virtual machine/instance, you’re also automatically creating a security group, which acts as a virtual firewall at the instance level.
A WAF, on the other hand, is only for HTTP(S) traffic and provides a much more sophisticated rule set. You can define conditions by using characteristics of web requests such as:
-
-
- Country that requests originate from
- Values in request headers
- Strings that appear in requests
- Length of requests
- Presence of malicious SQL code
- Presence of malicious script
-
As a result, a WAF can protect you from the following common attack types, which can’t simply be blocked by listing static ports/IPs in ACLs:
-
-
- UDP floods
- SYN floods
- HTTP floods
- SQL injection
- Bad bots
- Spoofing
-
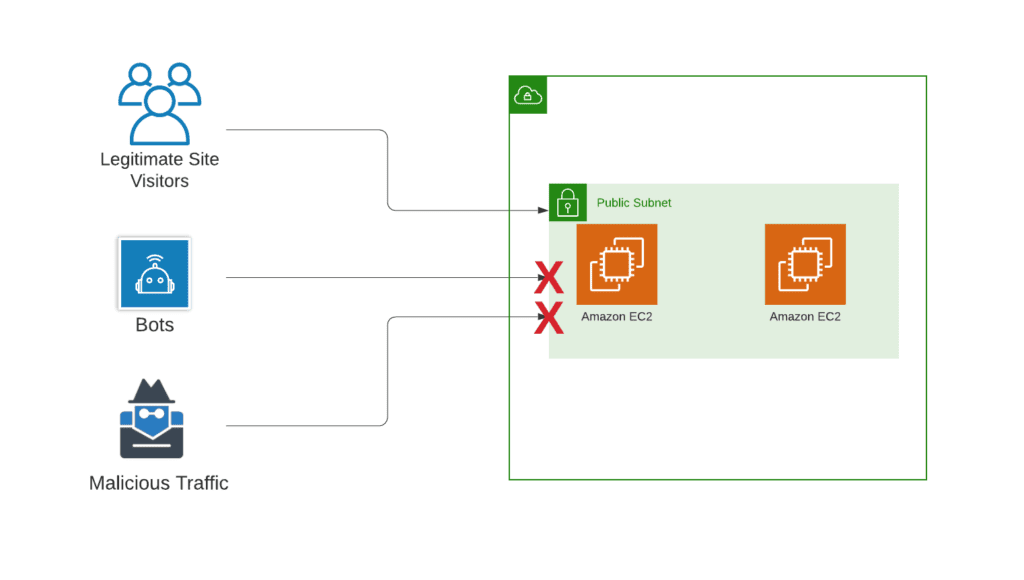
One of the other biggest differences between ACL and a WAF is that a WAF sits in front of your load balancer/CDN, whereas an ACL sits behind your load balancer/CDN, right at the subnet level. A WAF mitigates attacks before they reach your application. This is easiest to see in a diagram:
With WAF:
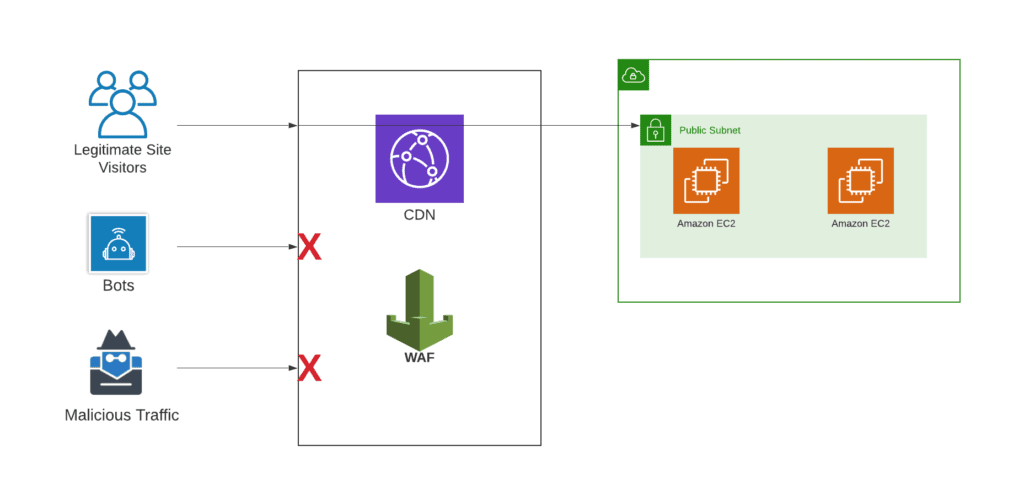
With Network ACLs configured to block common bot/malicious traffic IPs:
What about premium DDoS protection services?
Layer 3 and 4 DDoS attacks are usually large in volume, have clear signatures, and protection against them is automatically provided by major IaaS platforms (AWS Shield, Azure DDoS Protection Basic). But attacks at Layer 6 and 7, or application layer attacks, tend to be more sophisticated and focus on critical parts of the application. A WAF, when combined with your DNS service and CDN, can mitigate these types of attacks.
Cloud platforms also sell more advanced DDoS protection (AWS Shield Advanced, Azure DDoS Protection Standard), which also provides availability guarantees and a DDoS rapid response team — essentially a team of engineers to help you in case of a DDoS attack.
How hard is a WAF to set up?
Setting up a WAF requires significant knowledge of networking principles, and is best left to your networking team. It’s not an out-of-the-box service, despite cloud providers’ marketing claims.
First, setup your WAF in “count” mode in order to observe and identify normal traffic patterns. Use Managed Rules, which includes a curated set of rules that provide protection against the most common web exploits. These rules are maintained by your cloud provider, ensuring that the WAF service is kept up-to-date with the latest threats, known malicious IPs and URLs, and most recent attack patterns. Once a baseline is established, then you can fine-tune the Managed Rules before switching the WAF into block mode, providing continuous protection from web threats.
Does a WAF or DDoS protection guarantee that I won’t get hacked?
Unfortunately, no tool is perfect and many real attacks will happily pass through your WAF. But you can use WAF to mitigate OWASP’s Top 10 Web Application Vulnerabilities, and that’s a significant amount of protection.
How much do each of these options cost?
Standard network ACLs and security groups are free. Cloud platforms charge for your WAF based on the number of web ACLs, the number of rules, and the web requests you receive. Here at Logicworks we help dozens of companies run WAFs, with the average cost at around $400-500/month.
Both AWS and Azure’s advanced DDoS protection costs about $3,000/month, so significantly more than a WAF.
So…is a WAF worth it?
Long story short: a WAF is a relatively inexpensive way to get a lot of protection from common web exploits. If you’re running a mission-critical web application, it’s a must.
Logicworks is a cloud services provider that builds and manages complex infrastructure on AWS and Microsoft Azure. To learn more about our services, including our security services, contact us.


No Comments