In a cloud environment, where multiple users have access to creating and managing cloud resources, human error is inevitable. In fact, Gartner estimates that 99% of cloud security breaches will be a result of internal user error.
It’s not enough to just write up your security and governance policies in some documentation and hope people follow it; you need to build guardrails and automated procedures that ensure standards are maintained. This is the core purpose of Azure Policy.
What is Azure Policy?
Azure Policy is a free Azure service that allows you to create policies, assign them to resources, and receive alerts or take action in cases of non-compliance with these policies.
Azure Policy allows you to ensure that all resources are configured with required services, and will tell you when systems are out of compliance. So if you want all of your resources to be configured with Azure Backups, for example, it will either alert you when a VM doesn’t have Azure Backups configured or can automatically configure Azure Backups on that VM.
Azure Policy is used by 100% of Azure’s top 300 enterprise users and is a critical part of any mature Azure deployment. As part of a broad Azure governance practice, Azure Policy ensures that people beyond your central IT team (i.e. developers and LOB teams) can still have access to cloud resources, and can launch resources on demand, without sacrificing security and compliance.
The basic building blocks of Azure Policy are:
- Policy definition: Describes resource compliance and what effect to take when resource in non-compliant. (JSON)
- Example: Restrict the list of locations where users can deploy resources.
- Initiative: A collection of policy definitions that all contribute towards one overarching goal.
- Example: All policies that relate to billing can be grouped in one initiative.
- Policy or initiative assignment: Describes where the policy is applied. Can be a resource group or subscription.
- Example: The policy to limit the list of locations where users can deploy resources is applied only to the finance team’s resource group, and not to the Dev team’s resource group.
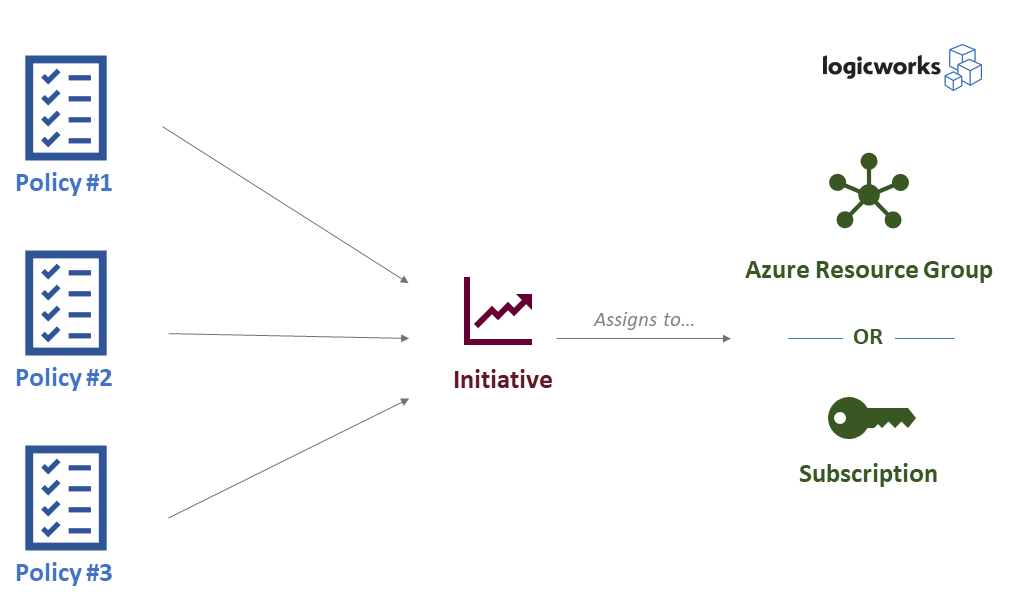
Example Azure Policy structure. Source: Logicworks
How to Apply a Policy in Azure Portal
To get started with Azure Policy, explore these tutorials and labs:
- Tutorial: Create and manage policies to enforce compliance
- Tutorial: Manage tag governance with Azure Policy
- Documentation: Remediate non-compliant resources with Azure Policy
- A Cloud Guru: Security and Governance in Azure (subscription required)
- Linux Academy: Hands-on Lab on Azure Policy (subscription required)
Examples of Azure Policy
- Apply tag and its default value
- Approved VM images
- Allowed SKUs for Storage Accounts and Virtual Machines
- Ensure storage file encryption
- Ensure https traffic only for storage account
How is this different from RBAC?
Role-based Access Control is about limiting which users can do what. Azure Policy is about limiting what actions can and cannot be taken. It doesn’t really care about what kind of user you are; if the Policy says you can’t open a certain port to the world, then you can’t.
Getting Started: Recommendations for Azure Policy
Honestly, you could write an entire book on Azure Policy and how best to use it to maintain your Azure infrastructure. It’s really at the heart of many foundational best practices about Azure.
But for the purposes of this post, we’ll just highlight a few of the critical areas you need to consider as you begin to explore Azure Policy, and direct you to some excellent resources and documentation as you keep learning.
Rely on a cloud security framework as a starting point, before you try to set any rules in Azure Policy. Many organizations begin cloud governance discussions simply by translating their on-premises governance policies to the cloud. As we explain in our blog post Security Risks in Public Cloud, you’re setting yourself up for failure. There are risks that were once critical in your datacenter, that are now less important in public cloud. More importantly, new risks arise in public cloud that you never had to think about in your datacenter. As we move beyond the simplistic understanding of “public cloud is secure / not secure”, we need a more nuanced understanding of how to best identify the real risks that deserve your attention.
Whether you build your own cloud corporate governance model, rely on a compliance framework like PCI or SOC, or use a well-regarded security framework like IANS or CIS, make sure you’ve established organization-wide policies first before you even start working on Azure Policy.
As you start using Azure Policy, handle non-compliant resources with alerting (audit effect) rather than action. This will allow you to make sure your policy definitions are correct before you let automation (potentially) wreak havoc off false positives.
Remember: the initial learning curve is high. Writing governance-as-JSON takes some getting used to, especially if you don’t have a ton of experience in similar work. There aren’t many examples and troubleshooting threads on Stack Overflow or other reference sites. Don’t just jump in thinking you’ve got this — read the documentation, take your time.
Last Thoughts
Azure Policy is an extremely powerful tool for Azure administrators. As you dig in, we encourage you to start small and mature your environment as you get more familiar with Azure.
If you have questions about Azure Policy or want help building or optimizing your Azure environment, reach out to the team at Logicworks. We’re Microsoft Gold Certified Partners and Azure Expert MSPs with 25 years of experience in IT consulting. Contact us.


No Comments